As we’ve stated in previous blogs, cyber recovery is arguably the most critical capability any IT decision-maker must evaluate when looking to modernize and transform their data protection to address today’s threats. It has become table stakes for data protection vendors to offer some cyber recovery features within their products, but not all cyber recovery protection is created equally.
Let’s be crystal clear about this. Settling for “Good Enough” is not an acceptable approach when it comes to protecting your company’s most critical data from a cyberattack. Would you settle for “Good Enough” safety in your automobile? Would you settle for “Good Enough” homeowner’s insurance to protect your house or family against a personal loss? If the answer is no, then when it comes to the data and applications that keep your business running and alive, why is “Good Enough” acceptable?
Some vendors claim that certain features or strategies are good enough in the face of a cyberattack, but they won’t be the ones left to answer the hard questions after an attack that leaves you unable to recover critical data. That will be you, your CEO, CFO, and CISO. That’s why if I were evaluating cyber recovery solutions, I would focus on the three cyber recovery pillars below to see which vendors truly help protect my company’s most critical asset.
Retention lock prevents specified files from being overwritten, modified, or deleted for a user-defined retention period and is an excellent first step for companies looking to improve their cyber resilience. Most vendors, including Dell Technologies, offer this hardening feature; but we take this protection even further. The Dell EMC PowerProtect DD retention lock feature, which has been attested to comply with the SEC 17a-4(f) standard, is a standard feature that comes in two flavors: Governance and Compliance mode. With Governance mode, data is retained for a specific time period, but can still be overridden or modified by an administrator with account credentials – this is valuable in certain use cases such as legal hold. Compliance mode, on the other hand, is stricter, and not even an administrator with (advanced) credentials can edit or delete data during the retention period. PowerProtect DD also includes Compliance Mode, for data protected within the cyber recovery vault, as a standard feature; there is no extra cost or performance penalty for being better protected!
At Dell Technologies, we’re advocates of Retention Lock, and that’s why we offer two modes. It’s a helpful first step in data hardening, but it’s still only one step of your cyber recovery strategy.
Cybercriminals’ techniques are continually evolving and becoming more advanced. In most cases, they will penetrate networks long before they launch their attack. Once inside the corporate network, they ensure that when they do strike you won’t be able to recover. They do this by disabling backups, changing NTP clocks, encrypting CIFS and NFS backup shares, and so on. This is why it is so necessary to have an off-network air gapped copy of your mission-critical data, ensuring you have a protected copy available in the event of an attack.
If you search for air gap solutions online, you will see most vendors in the market claim to offer some sort of a solution, but the devil is in the details. Everyone has a different definition of an air gap, including simply sending data offsite with tape. While it is correct that sending a tape off site provides an air gap copy, it comes with multiple tradeoffs. Minutes count in the event of a ransomware attack, and the time spent retrieving tapes from an offsite facility and then restoring your entire backup environment from tape will be costly. Another risk is that the backup catalog and tape media catalog may be compromised as part of the attack, rendering the offline tapes useless for recovery or needing to be re-indexed, which adds significant recovery time.
Moreover, depending on how old the tape is you need to recover, will you even be able to restore it? We all know tape degrades over time. Why would you want to risk putting your company’s most critical data on media that you know is susceptible to failure?
Recently, some vendors have even been positioning the idea of sending immutable copies, or data that is unable to be changed, to a public cloud as an air gap cyber recovery solution. The data sent to the cloud might be immutable, but your cloud account certainly isn’t. All it takes is an administrator with the right credentials (which a cyberattacker is likely to have since they already compromised the network) to delete your cloud account, not necessarily the files or content contained within that account, and that air gap copy in the cloud is gone.
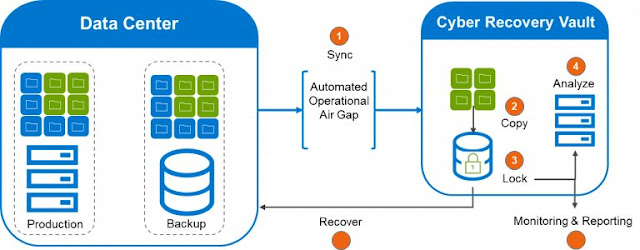
Dell EMC PowerProtect Cyber Recovery, on the other hand, provides an automated off-network air gap to provide complete network isolation. PowerProtect Cyber Recovery moves critical data away from both the production and backup environments attack surface, physically isolating it within a protected part of the data center (or offsite) and requires separate security credentials for access. This isolated environment, separated by the air gap, is what we call the PowerProtect Cyber Recovery vault, which is the centerpiece of our solution. The PowerProtect Cyber Recovery vault provides multiple layers of protection to provide resilience against cyber-attacks, even from an insider threat. PowerProtect Cyber Recovery automates the synchronization of data between the primary backup system and the vault, creating immutable copies with locked retention policies. If a cyberattack occurs, you can quickly identify a clean copy of your data and recover your critical systems to get your business back up and running. We can also support third party software paired with PowerProtect DD, which provides customers and partners flexibility and choice.
While many vendors in the market provide integrated analytics within their data protection solution, it’s important to understand what those analytics offer. As I have previously stated, most vendors only take a high-level view of the data and use analytics that looks for obvious signs of corruption based on metadata. Metadata-level corruption is not difficult to detect, and if a solution leverages this kind of analytics only, it will miss changes within the file itself that often indicate a compromise. Some vendors will also use a multi-pass approach that uses on-prem metadata analytics on the first pass, and then sends suspicious data to the cloud for a second pass of full content analytics. This approach, however, still has multiple challenges, including the delayed discovery of potential threats which forces the customer to send business-critical data offsite to a cloud provider, which is inherently less secure than performing these operations within the security of an on-premises vault environment.
PowerProtect Cyber Recovery not only provides full-content analytics but also operates inside the vault, where an attacker cannot compromise them. Running analytics on the data in the vault is a critical component to enable quick recovery of “known good data” after an attack. Our analytics are particularly powerful because they can read through the backup format. Hence, there is no need to restore data and PowerProtect Cyber Recovery can evaluate the full contents of the file, not just its metadata. To truly understand how powerful our analytics is, it’s essential to know how it works.
Data is first scanned in the format it was stored in the vault, typically this is a backup file format. Analytics then conduct over 100 observations per file. These observations are collected and evaluated by a machine learning tool that has identified patterns indicating data has been corrupted. Since we are looking for patterns and not signatures, the analysis is more effective and does not need to be updated as frequently. This process is repeated each time a new data set is brought into the vault. Data can be compared daily to provide a complete picture of changes that might be occurring very slowly and that other tools would likely miss.
In our opinion, along with a growing list of happily protected customers, PowerProtect Cyber Recovery provides the “best” protection against cyber attacks vs. many vendors who offer their “Good Enough” solutions.
Understanding these three cyber recovery pillars will help you make an informed cyber recovery decision that meets your company’s needs when you’re comparing solutions from different vendors. “Good Enough” might be acceptable when it comes to shopping at the grocery store, but not when it comes to deciding on cyber protection that impacts your company’s most valuable asset – data.
Let’s be crystal clear about this. Settling for “Good Enough” is not an acceptable approach when it comes to protecting your company’s most critical data from a cyberattack. Would you settle for “Good Enough” safety in your automobile? Would you settle for “Good Enough” homeowner’s insurance to protect your house or family against a personal loss? If the answer is no, then when it comes to the data and applications that keep your business running and alive, why is “Good Enough” acceptable?
Some vendors claim that certain features or strategies are good enough in the face of a cyberattack, but they won’t be the ones left to answer the hard questions after an attack that leaves you unable to recover critical data. That will be you, your CEO, CFO, and CISO. That’s why if I were evaluating cyber recovery solutions, I would focus on the three cyber recovery pillars below to see which vendors truly help protect my company’s most critical asset.
Retention Lock in Production
Retention lock prevents specified files from being overwritten, modified, or deleted for a user-defined retention period and is an excellent first step for companies looking to improve their cyber resilience. Most vendors, including Dell Technologies, offer this hardening feature; but we take this protection even further. The Dell EMC PowerProtect DD retention lock feature, which has been attested to comply with the SEC 17a-4(f) standard, is a standard feature that comes in two flavors: Governance and Compliance mode. With Governance mode, data is retained for a specific time period, but can still be overridden or modified by an administrator with account credentials – this is valuable in certain use cases such as legal hold. Compliance mode, on the other hand, is stricter, and not even an administrator with (advanced) credentials can edit or delete data during the retention period. PowerProtect DD also includes Compliance Mode, for data protected within the cyber recovery vault, as a standard feature; there is no extra cost or performance penalty for being better protected!
At Dell Technologies, we’re advocates of Retention Lock, and that’s why we offer two modes. It’s a helpful first step in data hardening, but it’s still only one step of your cyber recovery strategy.
“Off-network” Air Gap Isolation
Cybercriminals’ techniques are continually evolving and becoming more advanced. In most cases, they will penetrate networks long before they launch their attack. Once inside the corporate network, they ensure that when they do strike you won’t be able to recover. They do this by disabling backups, changing NTP clocks, encrypting CIFS and NFS backup shares, and so on. This is why it is so necessary to have an off-network air gapped copy of your mission-critical data, ensuring you have a protected copy available in the event of an attack.
If you search for air gap solutions online, you will see most vendors in the market claim to offer some sort of a solution, but the devil is in the details. Everyone has a different definition of an air gap, including simply sending data offsite with tape. While it is correct that sending a tape off site provides an air gap copy, it comes with multiple tradeoffs. Minutes count in the event of a ransomware attack, and the time spent retrieving tapes from an offsite facility and then restoring your entire backup environment from tape will be costly. Another risk is that the backup catalog and tape media catalog may be compromised as part of the attack, rendering the offline tapes useless for recovery or needing to be re-indexed, which adds significant recovery time.
Moreover, depending on how old the tape is you need to recover, will you even be able to restore it? We all know tape degrades over time. Why would you want to risk putting your company’s most critical data on media that you know is susceptible to failure?
Recently, some vendors have even been positioning the idea of sending immutable copies, or data that is unable to be changed, to a public cloud as an air gap cyber recovery solution. The data sent to the cloud might be immutable, but your cloud account certainly isn’t. All it takes is an administrator with the right credentials (which a cyberattacker is likely to have since they already compromised the network) to delete your cloud account, not necessarily the files or content contained within that account, and that air gap copy in the cloud is gone.
Dell EMC PowerProtect Cyber Recovery, on the other hand, provides an automated off-network air gap to provide complete network isolation. PowerProtect Cyber Recovery moves critical data away from both the production and backup environments attack surface, physically isolating it within a protected part of the data center (or offsite) and requires separate security credentials for access. This isolated environment, separated by the air gap, is what we call the PowerProtect Cyber Recovery vault, which is the centerpiece of our solution. The PowerProtect Cyber Recovery vault provides multiple layers of protection to provide resilience against cyber-attacks, even from an insider threat. PowerProtect Cyber Recovery automates the synchronization of data between the primary backup system and the vault, creating immutable copies with locked retention policies. If a cyberattack occurs, you can quickly identify a clean copy of your data and recover your critical systems to get your business back up and running. We can also support third party software paired with PowerProtect DD, which provides customers and partners flexibility and choice.
PowerProtect Cyber Recovery Analytics
While many vendors in the market provide integrated analytics within their data protection solution, it’s important to understand what those analytics offer. As I have previously stated, most vendors only take a high-level view of the data and use analytics that looks for obvious signs of corruption based on metadata. Metadata-level corruption is not difficult to detect, and if a solution leverages this kind of analytics only, it will miss changes within the file itself that often indicate a compromise. Some vendors will also use a multi-pass approach that uses on-prem metadata analytics on the first pass, and then sends suspicious data to the cloud for a second pass of full content analytics. This approach, however, still has multiple challenges, including the delayed discovery of potential threats which forces the customer to send business-critical data offsite to a cloud provider, which is inherently less secure than performing these operations within the security of an on-premises vault environment.
PowerProtect Cyber Recovery not only provides full-content analytics but also operates inside the vault, where an attacker cannot compromise them. Running analytics on the data in the vault is a critical component to enable quick recovery of “known good data” after an attack. Our analytics are particularly powerful because they can read through the backup format. Hence, there is no need to restore data and PowerProtect Cyber Recovery can evaluate the full contents of the file, not just its metadata. To truly understand how powerful our analytics is, it’s essential to know how it works.
Data is first scanned in the format it was stored in the vault, typically this is a backup file format. Analytics then conduct over 100 observations per file. These observations are collected and evaluated by a machine learning tool that has identified patterns indicating data has been corrupted. Since we are looking for patterns and not signatures, the analysis is more effective and does not need to be updated as frequently. This process is repeated each time a new data set is brought into the vault. Data can be compared daily to provide a complete picture of changes that might be occurring very slowly and that other tools would likely miss.
In our opinion, along with a growing list of happily protected customers, PowerProtect Cyber Recovery provides the “best” protection against cyber attacks vs. many vendors who offer their “Good Enough” solutions.
Understanding these three cyber recovery pillars will help you make an informed cyber recovery decision that meets your company’s needs when you’re comparing solutions from different vendors. “Good Enough” might be acceptable when it comes to shopping at the grocery store, but not when it comes to deciding on cyber protection that impacts your company’s most valuable asset – data.




0 comments:
Post a Comment