We have all seen the headlines with increasing frequency this past year and know them all too well. And because October is National Cybersecurity Awareness Month, we’re reminded that ransomware and cyber attacks have cost business billions, affected government and public services, and provided IT headaches to organizations. These sophisticated attacks use malware and methods that can quickly bring global operations to a standstill while encrypting or destroying critical data.
While these threats are increasing and getting more dangerous, customers are not always confident their runbooks and infrastructure are equipped with the right incident response and recovery procedures to bounce back from one of these attacks.
While these threats are increasing and getting more dangerous, customers are not always confident their runbooks and infrastructure are equipped with the right incident response and recovery procedures to bounce back from one of these attacks.
Data Protection infrastructure and architectures, commonplace in IT, are optimized for Operational Recovery, as well as Disaster Recovery providing excellent results and added business resiliency in scenarios such as natural disasters, system, or human error. However, counter to what other solution vendors in the marketplace would like you to believe, these systems are not a sufficient defense for sophisticated cyber attacks.
Disaster recovery does not equal cyber attack recovery
According to Gartner, traditional backup services are not designed for recovery from cyber attacks1. Gartner, along with other industry analysts, and several government agencies, recommend making backup images or gold copies inaccessible from the network through air-gapped media. Keeping gold copies of your essential business data protected away from the surface of attack is key to quicker business recovery and better resiliency.
The Cyber Recovery Solution from Dell EMC – a combination of hardware, software and professional services, assumes that you as a customer have optimized backup and disaster recovery infrastructure and procedures in place. Augmenting these optimized aspects of your data protection strategy with a Cyber Recovery Vault and automated data isolation workflow gives customers a last line of defense against ransomware and destructive cyber threats.
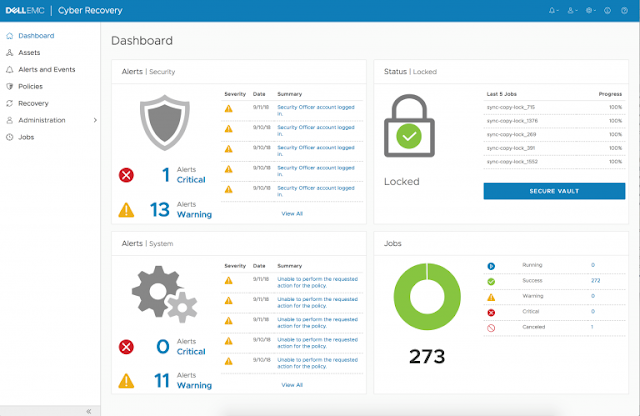
Introducing Dell EMC Cyber Recovery software
Today, Dell EMC is announcing further innovation and building upon the current Cyber Recovery Solution with the release of Dell EMC Cyber Recovery, which is easy-to-deploy management and automation software. Under the covers, Dell Cyber Recovery leverages industry-leading back-up technology from Dell EMC Data Domain including secure replication, data invulnerability architecture, retention lock, and data efficiency.
Modern UI/UX for management and automation
Dell EMC Cyber Recovery software provides a framework which automates workflows end-to-end, protects critical data within the Cyber Recovery Vault, helps identify malicious cyber-threats, and performs recovery when needed. At the center of this solution, a new REST API automation framework, provides seamless integration with a modern UI/UX.
The intuitive and clean design of the UI provides for faster environment status and easier orchestration of key workflow management tasks. Management and access via the UI and/or REST API is done from within the CR Vault, again keeping the solution’s management points away from the surface of attack.
Proactive analytics in the Vault
Customers can realize even greater benefit from our data isolation approach over other ransomware recovery solutions by performing security analytics on the retained data. Serving as the ideal test bed, the CR Vault allows customers to perform security analytics without having to perform a restore and potentially activating the malware. Dell EMC Cyber Recovery software was designed with flexibility rather than incorporating a proprietary and monolithic data analytics engine. It integrates with analytics tools that perform data scanning and early malware detection and reporting. Within the automation framework, analytics can be automatically performed on a scheduled basis.
Incorporating the power of Dell Technologies and its ecosystem partners further increases the value and power of Dell EMC Cyber Recovery through its flexibility. One example of this is Dell EMC’s partnership with Index Engines and its CyberSense security analytics tool.
CyberSense applies over 40 heuristics to determine indicators of compromise and can alert the user of potential problems. The rapidly changing threat landscape demands an adaptive analytics framework, so the solution stays ahead of the bad actor by enabling tools that incorporate Artificial Intelligence (AI) and Machine Learning (ML) analytics methods to the CR Vault.








0 comments:
Post a Comment