Since cyber attacks are increasing in frequency and sophistication — such as ransomware spread by phishing, which is hard to defend against — the need for large enterprises to protect their most important data has never been greater. Now you can help them protect their most important data with the Dell EMC Isolated Recovery solution, for another layer of defense-in-depth protection.
Hardware, Software and High-Margin Professional Consulting Services Needed
The Dell EMC Isolated Recovery solution requires hardware, software and high-margin professional consulting services to set up. It complements existing backup-and-recovery systems, which themselves can be subject to malware infection and data corruption simply via their 24×7 network connections.
What’s more, the unique Dell EMC Isolated Recovery solution is an extremely competitive offering. While many of our data protection competitors talk about hardened approaches to critical data, we have fully operationalized it. And this solution has many years of maturity and proven deployments behind it that you can use to help in your presentations to prospects.
Two of the world’s largest business consulting firms are already selling and deploying the solution to their large enterprise clients, generating professional services fees as well as commissions on Dell EMC data protection hardware and software. As a Dell EMC channel partner, you can find plenty of candidates for this solution among your own customers and prospects in virtually every industry, with a heightened awareness among these industries:
◉ Finance
◉ Government
◉ Education
◉ Healthcare
◉ Utilities
How the Dell EMC Isolated Recovery Solution Works
In short, the Dell EMC Isolated Recovery solution works by replicating a copy of backup data from the most critical applications to a physically and logically isolated and protected “gold copy.”
Once the update completes — in minutes or hours, depending on the change rate from the prior update and the total volume — the data streaming stops and automated software reestablishes an air gap between the source and target servers. It’s like opening and closing a vault door.
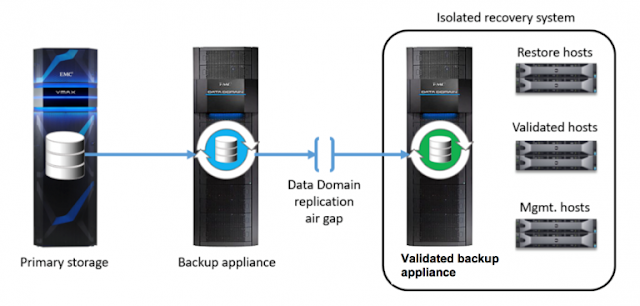
The diagram below illustrates how to implement this architectural approach using Dell EMC Data Domain hardware. (Note that Dell EMC VMAX servers or RecoverPoint appliances can also be used). The Data Domain hardware provides the capability to replicate data securely and asynchronously between systems with the connection air gap implemented when replication is idle. This isolates the replica Data Domain system, safeguarding a no-access vault copy of your critical data for the purposes of recovery.
Ultimately, the goal of the Dell EMC Isolated Recovery solution is to streamline the process of isolating a trusted gold copy of critical data, while keeping that copy updated. This will help enable the fastest possible recovery to a trusted state. Below are the four key elements of the Dell EMC Isolated Recovery solution:
◉ Isolation: The solution requires a physically isolated data center environment — sometimes called a vault — that is normally disconnected from the network and restricted to IT personnel with the proper clearance. It is normally located in a cage at the production site; no third site is necessary.
◉ Data copy and scheduled air gap: This core process is automated, using purpose-built software developed by Dell EMC, and manages the process of copying data to the isolated target. The software also manages the air gap’s scheduled window between the production environment and the isolated recovery zone. Automation is essential to managing the air gap and data movement.
◉ Integrity checking and alerting: These are workflows to stage copied data in the isolated recovery zone and perform integrity checks to rule out that it was affected by malware, and mechanisms to trigger alerts in the event of cyber attack or breach.
◉ Recovery and remediation: The solution includes validated procedures to perform recovery and remediation processes after an incident by leveraging a customer’s regular restore procedures, according to specific recovery point objectives (RPOs) and recovery time objectives (RTOs).
How to Sell the Dell EMC Isolated Recovery Solution
Talk to your customers and articulate the risks posed by Hacktivist Cyber-attacks. Highlight to them that the Dell EMC Isolated Recovery Solution leverages long proven EMC infrastructure and software and isolates their critical data from cyber-attack.





0 comments:
Post a Comment