Today’s factories are rapidly adopting new technologies to continue to improve operations, factory output and overall quality of the products they produce. In order to further optimize along Industry 4.0 concepts, it is important to extract data from production systems found in operational technology (OT) systems. These systems, which manage machines, robots, production lines and other systems doing the work on a factory floor, are often segmented and separate from traditional IT systems. The process of extracting, consolidating, analyzing and managing data from these systems provides insights that can lead to overall improvements for yield optimization, equipment effectiveness, production quality and other manufacturing outcomes.
Manufacturers may not realize the exposure they face, even with cyberattacks on the rise. But much like IT systems, OT systems also face threats. Firewalls and other enterprise security practices may not provide sufficient protection, or worse, manufacturers may think OT is not a target for cyberattacks in the first place. ICSs (industrial control systems) and other OT devices are often outdated, obsolete or designed without security features built in, as is the case with isolated network-connected devices.
Traditional IT security solutions may be unprepared for the challenges posed by OT. Tools that do well at protecting and monitoring IT systems simply do not have the visibility needed to find and identify malicious anomalies in OT. Coupled with a lack of expertise within organizations and resources to respond to incidents, disastrous consequences can occur.
A Holistic, Secure Manufacturing Portfolio
Manufacturers need a comprehensive, end-to-end security portfolio that can ensure cyber resiliency across IT and OT environments. Not all environments have the same needs and not all environments have modernized multifaceted security approaches to combat site, data and worker safety. For this reason, Dell Technologies leverages several solutions, including robust infrastructure delivered through secure supply chain, consulting and managed services, air-gapped data protection and integration with leading security software tools to achieve a holistic approach to securing the modern factory.
Dell Technologies designs, sizes and validates a security architecture for each customer’s unique factory floor needs. Our validated designs are engineered, purpose-built solutions created by our team of experts, who have years of experience in manufacturing cybersecurity. Lab validation helps deliver a solution that works for manufacturing organizations from day one. Manufacturing customers get a robust and secure architecture that reduces time to implementation, protects IT and OT systems and reduces vulnerability risk.
Our independent software vendor (ISVs) partners are leaders and innovators in their respective fields, bringing manufacturers the best IT and OT security solutions. Whether it’s running a production application critical to business operations or expanding an existing system seamlessly, Dell Technologies and our partners are ready to work toward a secure solution. Secure manufacturing products and services include:
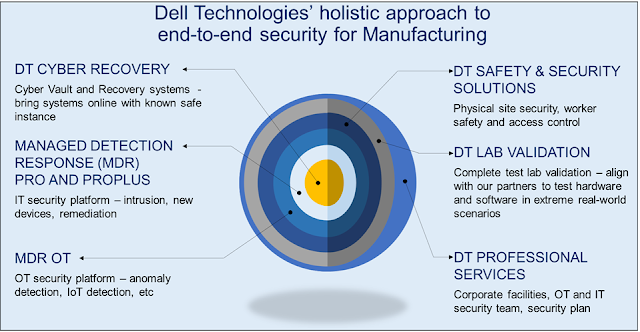
- Isolated, air-gapped backups with Dell PowerProtect Cyber Recovery. Synchronizes applications and data to an air-gapped, locked vault, which physically and logically isolates the data while software performs integrity check by analyzing data in the vault to ensure it’s free from manipulation or corruption.
- Managed detection and response. Checks device vulnerability, performs penetration testing and determines if the network can be accessed through OT devices; can also monitor for threats and perform remediation, when needed.
- Continuous monitoring with purpose-built OT platforms. Extends existing IT security controls to the OT environment for continuous monitoring of OT and industrial control system (ICS) devices; also performs deep-packet inspection and strategically integrates with MDR solution.
- Dell safety and security solutions. Combines Dell Technologies’ validated workloads for computer vision video analytics, video management systems (VMS) and access control systems on bare metal or hyperconverged infrastructures, along with partner-supplied appliances, in a scalable architecture. We work with a customer’s existing surveillance camera network, if possible, to simplify support, consolidate workloads and enhance surveillance systems with new capabilities like worker safety, site security, safe zones, enhanced access controls and other computer vision use cases.
- Secure supply chain. Dell Technologies’ desktops, servers, storage arrays and other hardware are “cybersecurity-hardened” in Zero Trust environments throughout development and manufacturing to delivery. Our multifaceted approach protects our supply chain, enabling us to deliver solutions that manufacturers can trust. Working together with Intel we can deliver the level of trust manufacturers need. Intel uses Compute Lifecycle Assurance (CLA), developed to extend trust throughout the product lifecycle, for example -Transparent Supply Chain, providing visibility from manufacture to deployment.
Dell Technologies Services helps customers at every phase of a secure manufacturing deployment. Our sales and security professionals assist customers in designing a cyber-resilient architecture they can trust to recover from a disruptive cyber event. PowerProtect Cyber Recovery services include advisory, design, deployment, implementation, test, recovery, operations and ongoing management of recovery services. Solution security analysts can assist with the initial setup, monitoring, detection, remediation, response and ongoing recommendations of improvements to keep security practices current. Each capability in the portfolio can stand on its own.
Some organizations have standardized on a cybersecurity solution leveraged by IT but may also look to extend their OT and IoT reach as they expand their Industry 4.0 projects. Isolating networks can provide additional security, which can be further enhanced through virtual network technologies. By integrating capabilities, OT security platforms can also integrate data from edge “listeners” to alerting and remediation in IT security tools, providing OT and IT flexibility to manage their preferred operations while centralizing alerting and response.
Finally, Dell Technologies’ secure manufacturing portfolio aligns with the Purdue Model framework for OT cybersecurity. Our digital safety model and validated designs can help manufacturers comply with industry standards and regulations, such as the ISO/IEC 27001 standard.
A Trusted, End-to-end Security Partner
Dell Technologies is a leading technology provider with a focus on both IT and OT, dedicated to helping manufacturers develop an enterprise-wide strategy to protect their operations from cyber threats.
It’s critical for manufacturers to proactively implement validated technologies that are supported by tested and documented recovery programs, to form a strong line of defense for the business. That’s what we provide and stand behind.
Source: dell.com





0 comments:
Post a Comment