In a matter of days, companies around the world showed incredible agility by moving from a limited remote workforce to a majority of their employees now working from home full time when their industries and work allowed. Because companies needed to act quickly, many established security standards were bypassed or hastily rushed through the process, increasing their exposure to cyber threats. Even the World Health Organization is warning against cyber attacks, citing a five-fold increase. This highlights that if you’re considering a data protection change, cyber recovery should be a key decision criteria that you validate before looking at other features and functionality. If the solution you choose does not allow you to quickly recover from all the different threats, including insider threats, then you could be putting your company at increased risk.
The first step is to establish your definition and goals for cyber recovery, depending on your company’s security needs and desired outcomes. In today’s data protection landscape, while it’s great that most vendors can provide strategies and features around cyber recovery, if they can’t help you accomplish your goals, then the solution is unusable. If I were evaluating a cyber recovery solution, I would ask these five questions to help understand which vendor can best support my definition and goals of cyber recovery and help me reach my long-term desired outcome.
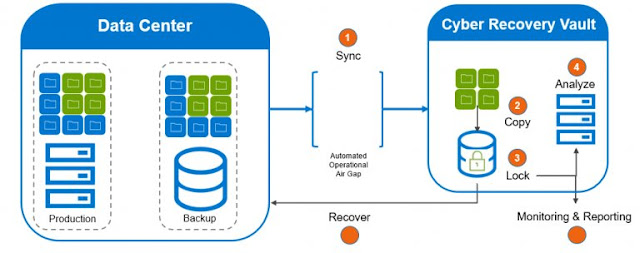
Without an isolated, logically air-gapped environment, data is vulnerable to threat factors. If the air gap is controlled from production, it’s vulnerable. If the air gap is opened and closed through a firewall or switch, it becomes a point of vulnerability, and the contents of the vault can be fully exposed when data is flowing.
Dell EMC PowerProtect Cyber Recovery provides a truly immutable, orchestrated, and automated logical air gap to protect data. The isolated vault components are never accessible from production, and access to the vault target is extremely limited. Some vendors will claim to offer an “air gap” solution because their data is separate from the production network or sent offsite to tape or the cloud. However, these strategies remain fully accessible to bad actors and don’t provide sufficient protection to a wide variety of threat actors, or efficient recovery mechanisms.
The first step is to establish your definition and goals for cyber recovery, depending on your company’s security needs and desired outcomes. In today’s data protection landscape, while it’s great that most vendors can provide strategies and features around cyber recovery, if they can’t help you accomplish your goals, then the solution is unusable. If I were evaluating a cyber recovery solution, I would ask these five questions to help understand which vendor can best support my definition and goals of cyber recovery and help me reach my long-term desired outcome.
1. Does the solution maintain a protected copy of data with physical and network isolation – a logical “air gap”? If so, how is the air gap opened and closed?
Without an isolated, logically air-gapped environment, data is vulnerable to threat factors. If the air gap is controlled from production, it’s vulnerable. If the air gap is opened and closed through a firewall or switch, it becomes a point of vulnerability, and the contents of the vault can be fully exposed when data is flowing.
Dell EMC PowerProtect Cyber Recovery provides a truly immutable, orchestrated, and automated logical air gap to protect data. The isolated vault components are never accessible from production, and access to the vault target is extremely limited. Some vendors will claim to offer an “air gap” solution because their data is separate from the production network or sent offsite to tape or the cloud. However, these strategies remain fully accessible to bad actors and don’t provide sufficient protection to a wide variety of threat actors, or efficient recovery mechanisms.
2. Does your backup software create or have access to the protected copy? Does your backup admin have access to the protected copy?
Some offerings in the market have data sets that reside in production and can be accessed by an administrator with appropriate credentials. An insider or advanced threat actor will likely have access to the backup server infrastructure. If that infrastructure includes access to the protected copy, it can be deleted or encrypted. How does this setup protect against a disgruntled employee looking to delete data or a threat actor who has stolen employee credentials from a previous attack?
PowerProtect Cyber Recovery has many layers to protect against advanced threat actors, including insiders. The vault itself is physically and logically isolated, and it cannot be accessed unless the person is physically in the vault. The vault also cannot be opened or controlled from the production side, so even an insider cannot gain access without physical access. Furthermore, in keeping with recommended best practices, only CISO-appointed administrators should have physical access to the vault. And this control can be further hardened through processes that – for example – require a second person when the vault is accessed to provide oversight.
3. Even if your solution protects data with “immutable” or “locked” storage, how do you protect it from an administrator? Do you require a secure time (NTP) source to protect the immutability?
Securing data against unauthorized changes or deletion is a good hardening practice, but it’s limited. While some immutability or locking capabilities are safe from regular users, an administrator can often override them. Vendors may claim that backups can never be changed, but they never say how this magic is performed. What happens if someone pulls drives, formats the appliance, or gains admin credentials?
Others are dependent on a time source that relies heavily on a secure Network Time Protocol (NTP) server. NTP is used by many components of the customer’s environment, like VMware, network, storage, and backup. What happens if a cybercriminal or insider compromises that server and moves the NTP date ahead past the lock period? PowerProtect Cyber Recovery not only provides a compliance retention lock capability that is attested to comply with the SEC 17a-4(f)(ii) archival standard but also uses an internal clock to help protect against attacks on an often vulnerable NTP server.
4. Do your analytics look at full content or just metadata?
Most vendors only take a high-level view of the data and use analytics that looks for obvious signs of corruption based on metadata. Metadata-level corruption is not difficult to detect, and if a solution leverages this kind of analytics only, it will miss changes within the file.
PowerProtect Cyber Recovery analytics go well beyond metadata-only solutions. The solution provides full-content based analytics, analyzing the file metadata, the document metadata, and the full content of the file itself – this is what sets PowerProtect Cyber Recovery apart from other vendors’ limited offerings. This solution uses more advanced capabilities such as the entropy (a measure of randomness) and similarity of the files. For example, a metadata-based analytics solution would not be able to determine that the contents of critical files have been encrypted if the file names have not been changed.
For added security, the analytics operates inside the vault, where an attacker cannot compromise them. This also provides the ability to enable a more efficient recovery after an attack. Competing analytics solutions simply don’t offer this level of intelligence or security. If they determine a file is suspicious based on their metadata scan, to do a full analysis, they must then send the entire file offsite to a cloud provider, where a second pass on the file can be performed. During a ransomware scenario where minutes count, this is a problematic strategy. Similarly, in a large-scale attack, network access could be destroyed or intentionally shut down, so it may not be possible to send the file(s) or obtain the results. Knowing which files have been compromised and which are safe to recover is critical knowledge before recovering data back into production environments.
5. Does your solution rely on a hidden share or view?
This is a strategy that looks better on a marketing one-pager than in the data center. Even if the data sets are “hidden,” they are still accessible to administrators. What’s stopping an insider threat from deleting these “hidden” data sets?
With PowerProtect Cyber Recovery, IT or Backup administrators can’t access or override security credentials or retention policies in the vault. You can rest assured knowing that you’re protected just as much from insider threats as from external ones.
Hopefully, thinking through these five questions and asking the vendors you’re evaluating how they handle these scenarios will help you make an informed Cyber Recovery decision that meets your company goals.





0 comments:
Post a Comment