Dell EMC Cyber Recovery Solutions at VMware VMUG Virtual Event (December 2018)
The number of successful Cyber Attacks are growing, and they are also evolving with more elaborate and innovative methods being used. As fast as organizations build defenses against attacks, hackers adapt and come up with new ways to work around them. Most organizations affected by these attacks have strong detection capabilities in place. The important question is however, could your organization recover if an attacker gets through the detection perimeter and encrypts or wipes your mission critical data? Organizations need to consider recovery as a vital part of their overall cyber-security and risk management strategy in order to truly become resilient in today’s cyber threat landscape.
Data Integrity and Cyber Recovery: Dell EMC and VMware
In our latest webinar, Dell EMC and VMware highlight how the latest security innovations from VMware vSphere and Dell EMC Cyber Recovery, leveraging Dell Technologies, it’s partners, and services can augment your overall cyber-security posture and provide a way to recover from a destructive cyber-attack.
Mike Foley, a Staff Technical Marketing Architect at VMware, described in great detail the latest security innovations which are a part of vSphere 6.7 Update 1. VMware is progressively hardening setting by default, ensuring work environments are protected and secure from Day 1. VMware is also able to transform endpoint detection and response with the ability to run AppDefense within the ESXi Hypervisor, allowing your company to respond to changing situations and concerns quickly with a secure infrastructure through visibility and control. By focusing on a new model of security, VMware is able to digest a simple and smaller problem set for a better sign-to-noise ratio, providing VMware AppDefense users with actionable and behavior-based alerts and responses to immediate cyber-attacks. Here is the Breakout Session.
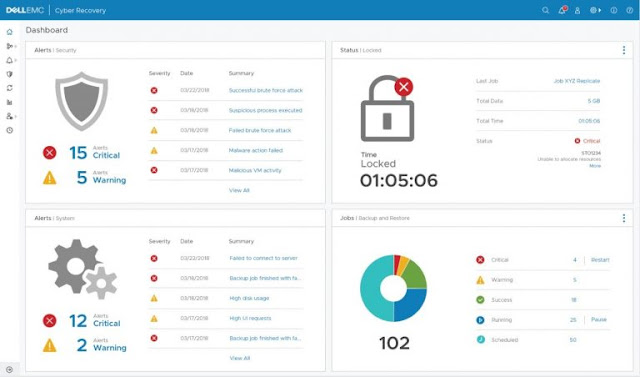
Alex Almeida, a Consultant Product Marketing Manager at Dell EMC, guided us through a comprehensive presentation on how Dell EMC allows companies to recover their VMware environments following a destructive cyber-attack. Today, 92% of organizations can’t detect cyber-attacks quickly enough, and 59% of organizations believe that isolating affected systems and recovering from backups should be the response to ransomware. Dell EMC Cyber Recovery is a comprehensive solution providing that vault and the newly announced Cyber Recovery 18.1 software brings end-to-end management of thissolution. Itruns entirely from within your data vault, giving your company the highest probability of clean data that is not infected or attacked to be secured for recovery. With Cyber Recovery 18.1, customers can benefit from end-to-end automated workflow, a modern & simple UI/UX, flexible REST API, and vault analytics with CyberSense workflow. Dell EMC also offers Dell EMC Services for Cyber Recovery solutions, providing organizations with deployment assistance, workshops, and advisory services to determine what solution and architecture is best for your company to be protected. Here is the Breakout Session.
So why Cyber Recovery from Dell EMC Data Protection?
Ensuring your business-critical data can withstand a cyber attack designed to destroy your data including backups and replicas. Here are the five steps to building a last line of defense.
1. Solutions Planning – Selection of application candidates, recovery time, and recovery point objectives.
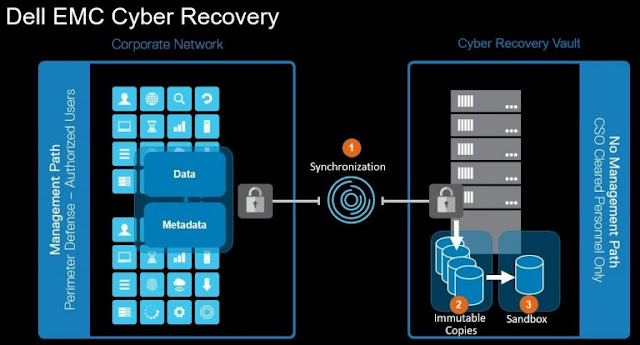
2. Isolation & Governance – An isolated data center environment that is disconnected from the network and restricted from users other than those with proper clearance.
3. Automated Data Copy and Air Gap – Software to create WORM-locked data copies to a secondary set of arrays and backup targets as well as processes to create an operational air gap between the production environment and the isolated recovery zone.
4. Integrity Checking & Alerting – Workflows to stage replicated data in the isolated recovery zone and perform integrity checks to analyze whether it is impacted by malware along with mechanisms to trigger alerts on suspicious executables and data.
5. Recovery & Remediation – Procedures to perform recovery / remediation after an incident using dynamic restore processes and your existing DR procedures.
Dell EMC Cyber Recovery, paired with VMware vSphere security, provides a very effective security and recovery solution against common attack vectors, including dormant malware, data wiping and locking, data corruption, insider attacks, and destruction of backup and storage assets. Simply put, it gives organizations an effective way to recover the lifeline of their business when other strategies fail.




thank for ur post , we give network switches suppliers in dubai
ReplyDelete