Many people have strong associations with the fall season: apple picking, colorful leaves, pumpkin (spice), playoff baseball. These activities invoke our senses to the point where we can feel the crisp air, taste the ball park mustard, and imagine the palette of leaves. The fall season invites you to create some great memories, and here at Dell EMC, we have 5 additional reasons to celebrate: five new PowerEdge servers!
This fall you could try something new. If you are interested in buying or trying the new servers, please contact your Dell EMC Rep or contact us directly. We also have some availability for remote or on-site trial of our new servers. Our Minerva cluster, 64 nodes of the C6525, creates an innovation sandbox for our HPC customers to test their ideas on the new PowerEdge servers with 2nd Gen AMD EPYC.
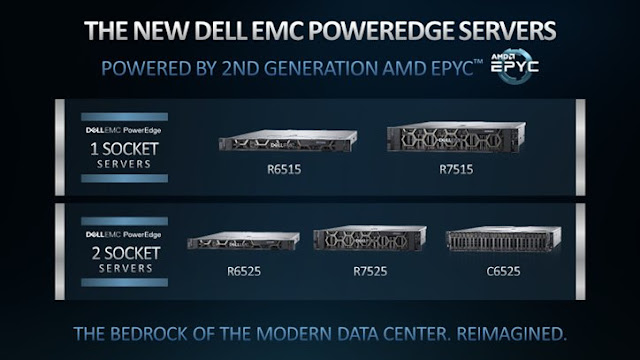
We announced our five new PowerEdge servers with 2nd Gen AMD EPYC processors on September 17th, with our 1-socket servers, the R6515 and R7515, ready for immediate sale. Now that that it is mid-October, two more solutions are ready to go along with some world records. The 2-socket PowerEdge servers, R6525 and C6525, are perfect solutions for data analytics, machine learning, and virtualization. Their optimized design gives businesses one of the most compute-dense servers in the industry. At Dell EMC, we wanted to make sure you enjoyed the season and leveraged these new solutions to handle critical and demanding workloads; think real-time sports analytics or high-performance hurricane modeling.
The PowerEdge server portfolio with 2nd Gen AMD EPYC provides more than just complex analytics workloads. The servers help any company manage their journey through their digital transformation, whether these solutions require software defined storage, virtualization, or high-performance computing (HPC). To build a sustainable competitive advantage, companies must cultivate these foundational capabilities from the ground up.
With the new PowerEdge servers, you can focus more time innovating, making strategic decisions, and creating value for your customers. The five new Dell EMC PowerEdge servers with 2nd Gen AMD EPYC provide world-record performance for whatever solution you are building.
Virtualize and Collaborate
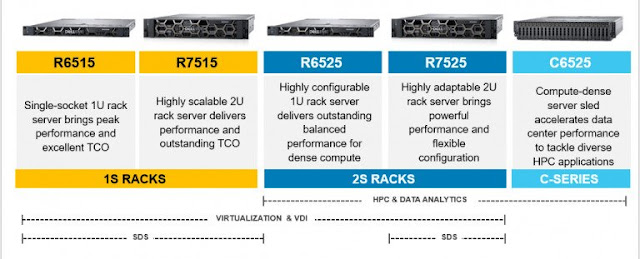
The new Dell EMC 1-socket servers, R6515 and R7515, are designed to increase collaboration and improve cost structure. The R6515 optimizes performance for virtual machine density, SQL, and hyperconverged infrastructure (HCI). Dell EMC built an Azure Stack for HCI Ready Node, so you don’t have to worry about optimizing your configurations. Instead, the R6515 saves time and money by allowing you to focus on collaboration and building applications for your hybrid cloud environment.
The R7515 is an amazing solution for database virtualization, especially for Hadoop and Spark. The R7515 has 8 world records filed for database virtualization; 4 in performance and 4 in price. Think of the time saved with 280% more throughput using MapReduce and a 51% IOPS increase on a vSAN Ready Node. On a 3-node cluster, the improvements in the R7515 translates to ~$269,000 in savings over an HPE DL380 3-node cluster. The R7515 helps create a competitive advantage for internal operations by improving data-backed decisions and significantly reducing the total cost of ownership.
Accelerate Performance
The new Dell EMC 2-socket servers, R6525 and C6525, are dense computing powerhouses, allowing for multiple accelerators. The R6525 increases SAP SD users by 37% with half the rack space of the HPE DL385. Talk about the ultimate ERP and business analytics solution. More users and less rack space are short cuts to TCO advantages and digital transformation. Your data center will have more space to run other workloads, allowing IT to create new innovative solutions. Just imagine the potential customer analytics, business research, and improved operations.
The C6525 was purposefully designed and built for high-performance computing and HPC Ready solutions. The C6525 has records in digital manufacturing as well as weather research and forecasting. Not to mention that the 202% increase in LINPACK GFLOPS ensures your superpowered weather models are also accurate. Again, we built the Ready Solutions to keep your mind on the important things; developing more accurate weather forecasts, constructing better economic projections, and designing a new airplane or car.
Test what these servers can do for you
Fall is the best time to make a change. As others prepare to hibernate during the winter months, you can be busy planning and building for the spring rebirth. Creating a competitive advantage starts with the foundation. The groundwork in digital transformation is the IT infrastructure used to support your workforce and your operations that eventually create value for your customers. Dell EMC PowerEdge servers with 2nd Gen AMD EPYC help our customers manage traditional and emerging workloads, cut deployment times, and boost security. Stay on the cutting edge of the digital transformation by building world class infrastructure.