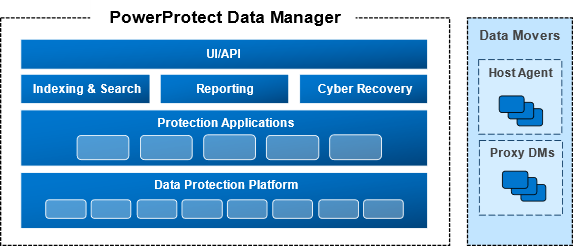
Figure 1: PowerProtect Data Manager high-level architecture.
Data Protection Platform
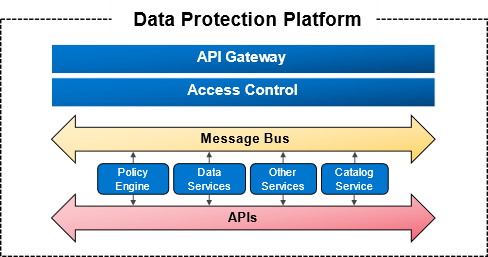
To support the scale of operations, breadth of capabilities and accelerated development, Dell has created a Data Protection platform (See Figure 2). The Data Protection Platform provides reusable, resilient and scalable infrastructure services to rapidly onboard new data protection workloads.
Figure 2: PowerProtect Data Manager- Data Protection Platform.
The Key Elements
Policy Engine
For large customer deployments with thousands of VMs or databases, prioritizing, scheduling and load balancing become crucial to ensure customers consistently meet SLAs.
Customers have varied needs to manage their protection copies, including creating a local operational copy or one or more remote copies to protect against disaster, tiering a copy to object storage for longer-term retention and making copies immutable for ransomware protection and ensuring they create and retain the copies to meet the business needs and costs.
A modern policy should be able to express these constraints in a simple and consistent way for all workloads. Automation delivers hands-off protection, which reduces administrative efforts and increases the platform’s efficiency and performance.
To support lower RPOs for protection, control path orchestrations overhead for protection need to be minimal since the amount of time spent in moving data from production to protection storage is in seconds or even minutes.
We built the Policy Engine to handle protection at enterprise scale, manage policies simply and consistently for all workloads and support lower RPOs. The Policy Engine is built to scale with minimal control path overhead in scheduling the protection. It ensures full and incremental log backups do not overlap and the protection is optimally ordered to meet the SLAs. It confirms the resources (e.g., PowerProtect DD series, vCenter, proxies, etc.) are optimally utilized, load-balanced and honoring any user defined constraints.
The Policy Engine’s design provides a simple way for admins to express their backup, replication, Cloud DR, cloud tiering, retention and immutable copy needs. Each protection copy creation is modeled as a protection stage with consistent scheduling and retention configurations. This protection stage user model is easy for Dell to add new capabilities.
Catalog Service
For Data Manager, a centralized catalog addresses the needs of the backup admin. The centralized catalog needs to scale and be responsive to search, aggregation and reporting, as well as be able to handle low RPO copies. Data Manager’s catalog service has been purpose-built to handle this scale and RPO needs while being responsive.
Self-service protection and recovery are key capabilities of Data Manager. We distribute the catalog across the various application agents, which remain synchronized with the centralized catalog. This catalog for self-service needs to be aligned with the catalog that is maintained by native self-service tool (e.g., Oracle RMAN). To provide additional resilience against various failures and to ensure the backups are always recoverable, the application agent catalog is also written to PowerProtect DD series appliances along with the backup data.
Data Manager includes a purpose-built deduplication Index and Search scale-out catalog, which supports search and recovery activities based on “name” and associated metadata. This catalog indexes every single file in copy (e.g., VM backups), while also minimizing the storage capacity needed to maintain this when you have hundreds of copies for a single protected asset.
Access Control
Cybersecurity and access controls are extremely important. At Dell, we have set Zero Trust as the North Star of our security strategy. We have diligently worked to enhance and align access control for PowerProtect Data Manager toward these goals.
As one of the Zero Trust tenets, Role-based Access Control (RBAC) lets you assign different “roles” to different users and inherently allows access control to sensitive data and operations. Instance-based Access Control (IBAC) works in conjunction with RBAC and provides very granular access control at object level to address the “trust nothing” paradigm from Zero Trust by explicitly allowing access to a set of resources.
You can select asset assignment rules via IBAC manually or automatically assign them. The assignment rules leverage native workloads constructs while providing a unified and consistent view for all workloads. To provide efficient and responsive operations without needing in-memory processing, we have built a multi-layered model for security where RBAC operations are validated at access-point and IBAC controls are handled at the lowest layer in the data model.
By providing a generic enforcement of RBAC/IBAC controls at the Platform layers, we have consistent controls across all protection workloads and simplified the Data Manager implementations.
PowerProtect Data Manager’s Data Protection Platform, Policy Engine, Catalog Service and Access Controls enable you to start your journey toward modern data protection. Please visit the Dell PowerProtect Data Manager solutions page for more details.
Source: dell.com





0 comments:
Post a Comment